C844 - Study guides, Class notes & Summaries
Looking for the best study guides, study notes and summaries about C844? On this page you'll find 94 study documents about C844.
Page 4 out of 94 results
Sort by

-
C844 grp1 task 1 nmap and wireshark, With Complete Verified Solution, 2024
- Exam (elaborations) • 11 pages • 2024
-
- $13.48
- + learn more
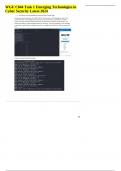
C844 grp1 task 1 nmap and wireshark August Voytek - C844 A. Describe the network topology… Figure 1 NMAP scan indicates that there are a total of 8 devices on the 192.168.27.0/24 network. Three devices are Windows-based systems, three devices are Linux based systems, and two had operating systems that were unable to be identified. The logical network topology can be described as a star topology. See Figure 1 above for the Zenmap s...

-
WGU C844 EMERGING TECHNOLOGIES IN CYBERSECURITY, Complete Solution 2024.
- Exam (elaborations) • 9 pages • 2024
-
- $12.49
- + learn more
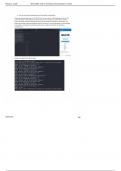
WGU C844 EMERGING TECHNOLOGIES IN CYBERSECURITY A. Wireless Local Area Network (WLAN) Vulnerabilities Within this section I will point specifically point out some of the potential Wireless Local Area Network (WLAN) vulnerabilities found during the initial review of the Alliah corporate headquarters. Even though these two vulnerabilities are the focus this WLAN Vulnerabilities section, a further, in-depth inspection and assessment may lead to others as well. Below are the two vulnerabilit...

-
WGU C844 EMERGING TECHNOLOGIES IN CYBERSECURITY
- Exam (elaborations) • 9 pages • 2024
-
- $10.99
- + learn more
1. WGU C844 EMERGING TECHNOLOGIES IN CYBERSECURITY Performance Assessment GRP-1 Task 2 Table of Contents A. Wireless Local Area Network (WLAN) Vulnerabilities. 2 B. Mobile Device Vulnerabilities. 2 C. Steps for Mitigation. 3 D. Preventative Measures. 4 E. Recommended Solution for Bring Your Own Device (BYOD). 4 F. Cited Sources. 5 A. Wireless Local Area Network (WLAN) Vulnerabilities Within this section I will point specifically point o...
-
Wgu c844 task 1 emerging technologies in cyber security, Updated 2024
- Exam (elaborations) • 6 pages • 2024
-
- $10.29
- + learn more
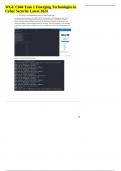
Wgu c844 task 1 emerging technologies in cyber security, Updated 2024 A. Describe the network topology that you found when running Nmap. 6 hosts were found using nmap -sn 10.168.27.0/24. The hosts are in a STAR topology as shown in the screenshot below. A star topology means that all hosts are connected to a central device, usually a switch. This makes it easier to add and take away new hosts with no disruption to the network. The switch also provides a central management point for all devic...

-
C844 task 1 passed 1st attempt exam guide 2024 top graded
- Exam (elaborations) • 7 pages • 2024
-
- $11.99
- + learn more
C844 Task 1 Mapping and Monitoring A. Nmap Topology The topology found using Zenmap is a Star topology (See Figure 1). It indicated there were 5 hosts connected to the switch, and at least one of them was running linux OS. A Star topology is when each computer or host is connected to one central point like a hub or a network switch. This is the most beneficial type of topology for a few reasons, being: Easy to connect new computers/hosts without affecting the rest of the network, centr...

-
C844 grp1 task 1 nmap and wireshark
- Exam (elaborations) • 11 pages • 2024
-
Available in package deal
-
- $7.99
- + learn more
C844 grp1 task 1 nmap and wireshark August Voytek - C844 A. Describe the network topology… Figure 1 NMAP scan indicates that there are a total of 8 devices on the 192.168.27.0/24 network. Three devices are Windows-based systems, three devices are Linux based systems, and two had operating systems that were unable to be identified. The logical network topology can be described as a star topology. See Figure 1 above for the Zenmap s...
-
WGU C844 Task 1 Emerging Technologies in Cyber Security Latest 2024
- Exam (elaborations) • 6 pages • 2024
-
- $14.99
- + learn more
WGU C844 Task 1 Emerging Technologies in Cyber Security Latest 2024. . Describe the network topology that you found when running Nmap. 6 hosts were found using nmap -sn 10.168.27.0/24. The hosts are in a STAR topology as shown in the screenshot below. A star topology means that all hosts are connected to a central device, usually a switch. This makes it easier to add and take away new hosts with no disruption to the network. The switch also provides a central management point for all devices...
-
WGU C844 Task 1 Emerging Technologies in Cyber Security Latest 2024/2025.
- Exam (elaborations) • 6 pages • 2024
-
- $16.49
- + learn more
WGU C844 Task 1 Emerging Technologies in Cyber Security Latest 2024. A. Describe the network topology that you found when running Nmap. 6 hosts were found using nmap -sn 10.168.27.0/24. The hosts are in a STAR topology as shown in the screenshot below. A star topology means that all hosts are connected to a central device, usually a switch. This makes it easier to add and take away new hosts with no disruption to the network. The switch also provides a central management point for all device...

-
WGU C844 EMERGING TECHNOLOGIES IN CYBERSECURITY
- Exam (elaborations) • 9 pages • 2024
-
- $12.98
- + learn more
WGU C844 EMERGING TECHNOLOGIES IN CYBERSECURITY Performance Assessment GRP-1 Task 2 Table of Contents A. Wireless Local Area Network (WLAN) Vulnerabilities. 2 B. Mobile Device Vulnerabilities. 2 C. Steps for Mitigation. 3 D. Preventative Measures. 4 E. Recommended Solution for Bring Your Own Device (BYOD). 4 F. Cited Sources. 5 A. Wireless Local Area Network (WLAN) Vulnerabilities Within this section I will point specifically point out some of the potential ...

-
WGU C844 Emerging Technologies in Cybersecurity Task 1 GRP1
- Exam (elaborations) • 11 pages • 2024
-
Available in package deal
-
- $6.99
- + learn more
TASK 1: NMAP AND WIRESHARK GRP1 TASK 1: NMAP AND WIRESHARK Emerging Technologies in Cybersecurity-C844 Western Governors University Jennifer Goodchild Student ID # # December 29, 2021 1 TASK 1: NMAP AND WIRESHARK A. The Network Topology After opening the root emulator and typing Zenmap, I ran a network scan of the domain 10.168.27.0/24. I selected the Quick scan plus option, then clicked scan. The network sc...

Study stress? For sellers on Stuvia, these are actually golden times. KA-CHING! Earn from your study resources too and start uploading now. Discover all about earning on Stuvia


